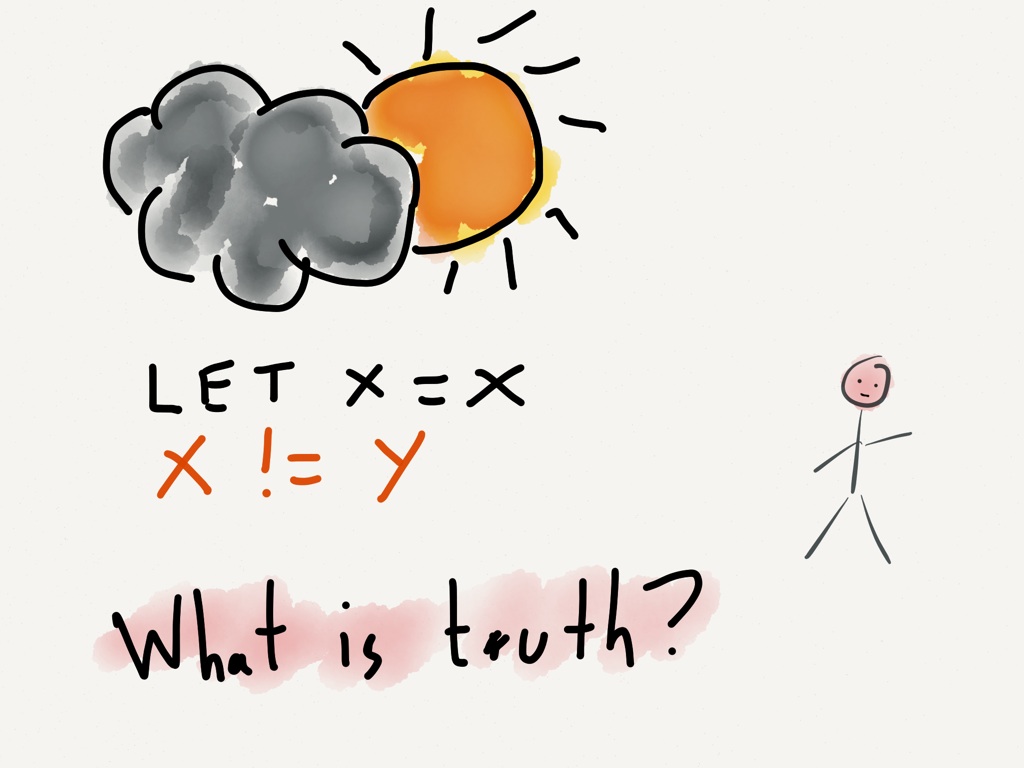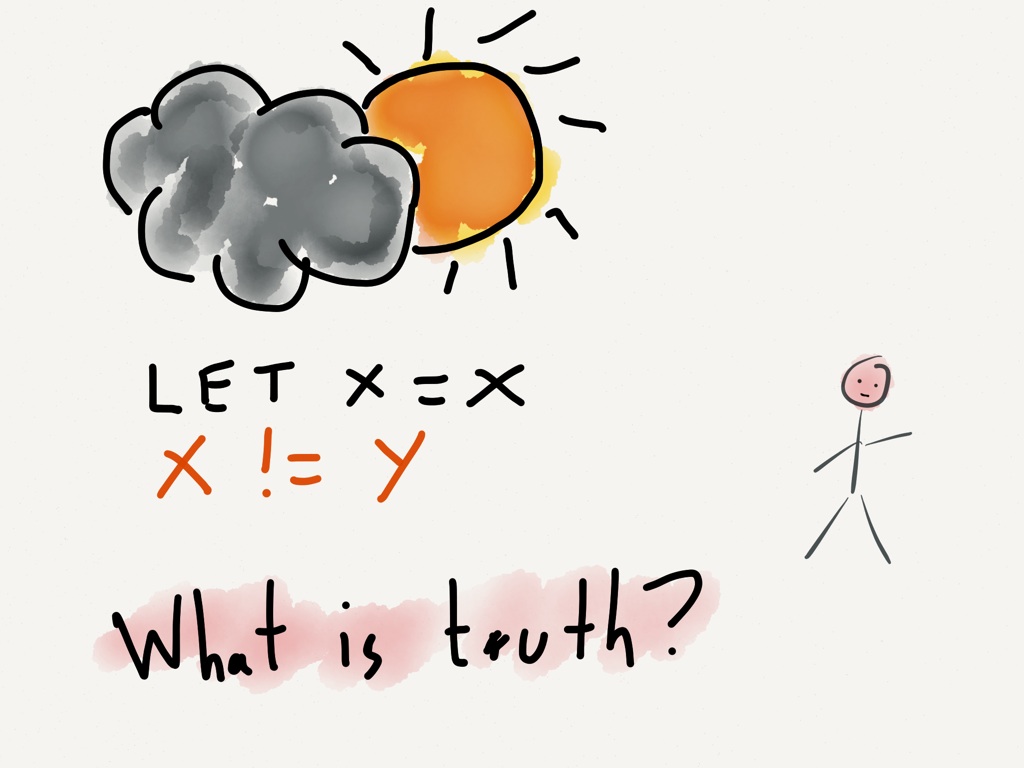Why do you debug your code? Because you seek the truth.
What is the truth? Code that works.
It’s impossible for a coder not to want to seek the truth, otherwise why would they waste time writing code that doesn’t work? Code must work. That’s the point of it. Thus, coders seek the truth. When we debug and trace, and spend days in search of the cause of a bug in our code, we are seeking the truth.
It therefore becomes ingrained in the coder to seek the truth at all levels. Perhaps this explains why we have whistle blowers and hackers that want to expose wrongdoing – Aaron Swartz, Julian Assange, Edward Snowden, and many others. When you spend your time seeking the truth in code, why would you not seek it elsewhere?
These people are not “hacking”, nor “whistle-blowing”, they are debugging. They’ve found an issue, and filed a bug report with reproducible test cases.
This begs the question – if coders seek the truth, what about non-coders? For example, certain so-called “managers”, or “directors”. These people get to the top of the greasy pole by obfuscation and lies. They operate behind closed doors, wheeling and dealing, bigging themselves up, putting their name to work that others have done, and continue to protect themselves by concealing the truth.
In terms of coding, they publish phony APIs that serve as a bogus front to private, undocumented methods and frameworks. Consequently, the organisational program becomes hampered by bugs, and any attempt to debug it by those suffering the consequences leads to accusations of “whistle blowing”, or “trouble making”.
If the organisation we belong to can’t be debugged because we’re being fed phony data, we leave.
After all, we seek the truth.